A Comprehensive Guide on Protecting Yourself from Phishing Attacks

In an era dominated by digital interactions, the threat of phishing attacks looms large. Cybercriminals continually refine their tactics to deceive unsuspecting individuals and organizations, making it crucial for everyone to understand and implement effective measures to protect against phishing. In this article, we’ll delve into the world of phishing attacks, exploring what they are, […]
Safeguarding India’s Industrial Automation: Addressing Challenges and Implementing Solutions

The industrial automation (IA) landscape in India, valued at approximately $11 billion in 2023, is poised for robust growth, projected to reach $23 billion by 2027. As this sector advances, so do the challenges in cybersecurity management, demanding strategic actions to fortify defenses. Cybersecurity Challenges in IA: The convergence of Information Technology (IT) and Operational […]
What is OAuth 2.0? How it actually works?
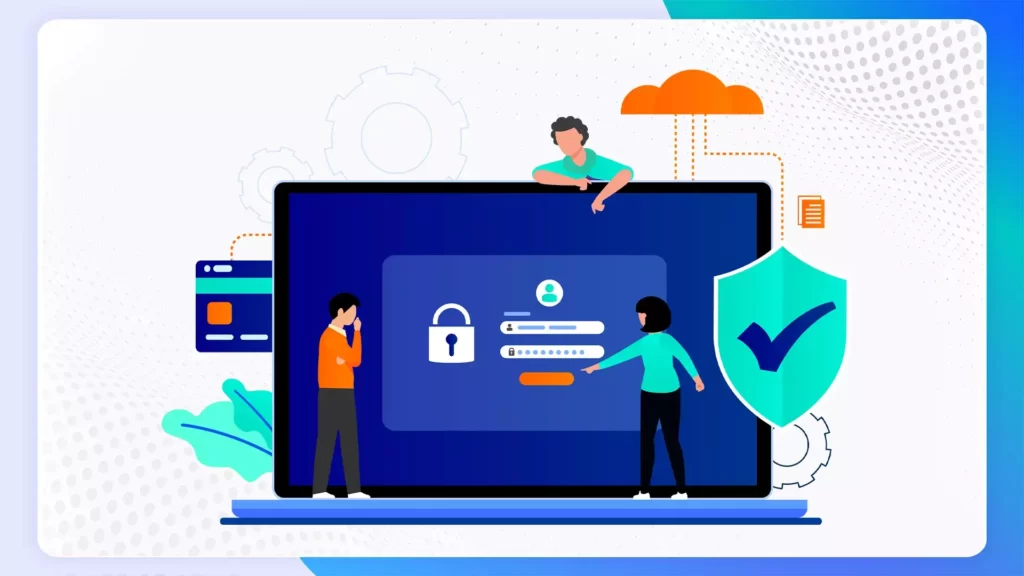
OAuth 2.0 (Open Authorization 2.0) is an industry-standard protocol for authorization that provides a secure and delegated access mechanism, allowing third-party applications to access a user’s data without sharing credentials. It is widely used for enabling secure access to APIs (Application Programming Interfaces) and ensuring that user credentials are not exposed to unauthorized parties. Here […]
What is Deepfake? Effective ways to prevent Deepfakes.

What is Deepfake? Deepfake is a type of fake content generated using advanced computer technology, especially artificial intelligence. It involves creating deceptive videos, images, or audio recordings that appear genuine but are entirely fabricated. Imagine a video where the face of a famous actor is seamlessly replaced with the face of someone else, making it […]
7 Powerful Strategies to Protect Yourself From Social Engineering Attacks

In an age where information is power and digital communication is the norm, the threat of social engineering attacks looms larger than ever. Whether you are an individual or a business, understanding and defending against these deceptive tactics is crucial for safeguarding your personal information and sensitive data. Social engineering attacks represent a significant and […]
What is Phishing? Top 10 Ways to Prevent Phishing

In today’s digitally interconnected world, where information is a prized asset, cybersecurity threats continue to evolve. A significant threat that can cause substantial harm to both organizations and individuals is “Phishing”. In this beginner’s guide, we will explain what is Phishing, its various types, the techniques employed by cybercriminals, and the crucial ways to protect […]
5 Vital Insights: What is Spyware and How to Shield Your Devices

In the contemporary era of technology, our devices are seamlessly integrated into our everyday routine. However, with the convenience of technology comes the risk of online threats, and one such threat that often goes unnoticed is spyware. In this beginner’s guide, we will explore the world of spyware; what is spyware, its implications for user […]
Boost Your Organization’s Defense: Strengthening Security with Phishing Simulation

In today’s interconnected digital world, phishing attacks have become a formidable threat, targeting organizations of all sizes and industries. These attacks can lead to data breaches, financial losses, and reputational damage. Traditional security measures alone are no longer sufficient to combat the sophistication of modern phishing tactics. That’s why our advanced-level Phishing Campaign Simulations offer […]
Emerging Trends in Cybersecurity: Leveraging Quantum Technologies

In today’s rapidly evolving digital landscape, staying ahead of cyber threats is a paramount concern for organizations of all sizes. As cyberattacks become more sophisticated and pervasive, cybersecurity professionals need to explore innovative solutions to fortify their defenses. One of the most intriguing and promising advancements in this realm is the integration of quantum technologies […]
Unveiling the Power of Threat Hunting: Why It’s Crucial for Your Cybersecurity Strategy

In the ever-evolving landscape of cybersecurity, the concept of “Threat Hunting” has emerged as a proactive and essential approach to safeguarding digital environments. This blog post aims to demystify the concept of threat hunting, shedding light on its importance in defending against emerging cyber threats. What is Threat Hunting? Threat hunting is the practice of […]
