Embracing the Mobile Revolution: The Explosion of BYOD and Mobile Devices

In today’s digitally connected world, the proliferation of mobile devices has transformed the way we work, communicate, and access information. One significant shift in the technology landscape has been the widespread adoption of Bring Your Own Device (BYOD) policies. This trend has unleashed a wave of productivity, flexibility, and convenience, allowing employees to use their […]
Embracing the Future of Cybersecurity: Zero Trust Architecture Unveiled

In an era where cyber threats are becoming more sophisticated and pervasive, traditional security approaches are no longer sufficient to protect sensitive data and critical systems. Enter Zero Trust Cybersecurity, the revolutionary concept that is reshaping the landscape of digital defense. In this blog, we will dive into the world of Zero Trust, unravel its […]
Insider Threats-Safeguarding Your Organization Against the Hidden Enemy

In the realm of cybersecurity, external threats often steal the limelight, but it’s essential not to overlook the lurking danger from within. Insider threats, posed by employees or trusted individuals within an organization, can lead to significant data breaches, financial losses, and reputational damage. This blog post sheds light on the growing menace of insider […]
State-Sponsored Cyber Warfare
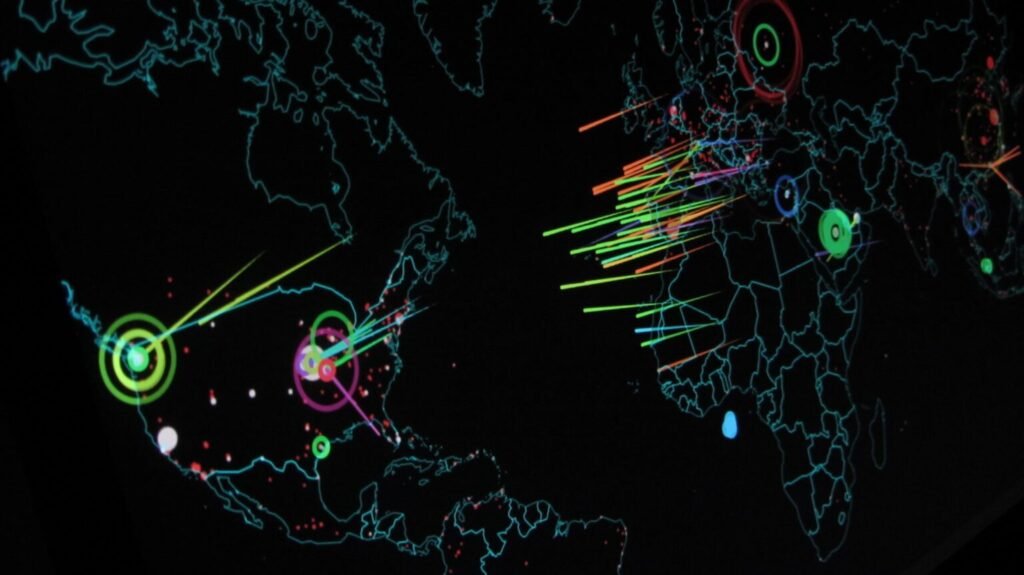
State-sponsored cyber warfare has emerged as a formidable and pervasive threat in the digital age. This blog post delves into the alarming world of state-sponsored cyber attacks, revealing the latest statistics and shedding light on the evolving global threat landscape. Brace yourself as we uncover the hidden dangers and geopolitical ramifications of this sophisticated form […]
IoT With 5G Network: The New Era of Technology and Risks

In recent years, the combination of Internet of Things (IoT) and 5G network technology has opened up a new realm of possibilities for innovation and connectivity. The seamless integration of IoT devices with the high-speed, low-latency capabilities of 5G networks promises to revolutionize various industries. However, this convergence also brings forth new cybersecurity risks that […]
Data Breaches: Prime Targets in the Cybersecurity

In today’s digital age, data breaches have become a pressing concern for organizations and individuals alike. Cybercriminals are constantly evolving their techniques to exploit vulnerabilities in systems and gain unauthorized access to sensitive information. This blog explores the alarming rise of data breaches and sheds light on why they have become prime targets in the […]
Cloud is Also Potentially Vulnerable

In recent years, the widespread adoption of cloud computing has revolutionized the way businesses operate and manage their data. However, amidst the countless benefits, it’s crucial to recognize that the cloud is not immune to vulnerabilities. This blog post delves into the potential security risks associated with cloud environments and explores effective strategies to mitigate […]
Mobile is the New Target: Securing Your Devices in the Mobile Age

In today’s technology-driven world, mobile devices have become an integral part of our lives. From smartphones to tablets, we rely on these devices for communication, entertainment, and even business transactions. However, with the increasing popularity of mobile devices, they have also become a prime target for cybercriminals. In this blog post, we will explore the […]
Unleashing the Power of Artificial Intelligence in Cybersecurity: A Game-Changer for the Digital Age

In recent years, Artificial Intelligence (AI) has emerged as a transformative technology, revolutionizing various industries and unlocking new possibilities. With its ability to simulate human intelligence, AI has the potential to reshape the way we live, work, and interact. In this blog post, we will explore the top trending keywords surrounding the potential of AI […]
The Rise of Automotive Hacking: Safeguarding Our Connected Cars

In today’s interconnected world, where technology is advancing at an unprecedented pace, even our vehicles have become vulnerable to cyber threats. The rise of automotive hacking has brought forth critical concerns regarding the security and safety of modern vehicles. This blog post delves into the emerging landscape of automotive cybersecurity, highlighting the challenges, potential risks, […]
